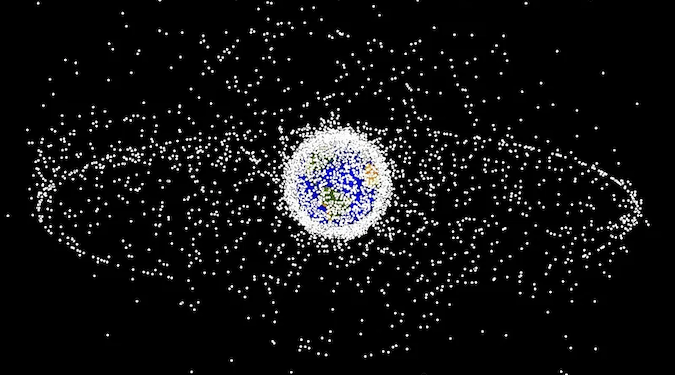
Matin Pedram and Eugenia Georgiades compare existing regulatory frameworks for Low Earth Orbit (LEO) satellites and argue none are robust, transparent, or efficient enough yet to curb monopolistic or rent-seeking behaviors. Likewise, Pedram and Georgiades reveal how national security concerns can be overextended to instead protect domestic space activities. Pedram and Georgiades analyze licensing requirements,… Continue reading The Role of Regulatory Frameworks in Balancing Between National Security and Competition in LEO Satellite Market
Tag: National Security
Will Soper Responds to Tyler Smotherman’s Review of “Greytown Is No More!”
I have read Tyler Smotherman’s review of my book, Greytown Is No More! I am much buoyed by the many positive passages to be found throughout its 17 pages. I wish to thank the reviewer, Tyler Smotherman, JNSLP Managing Editor Todd Huntley, and Editor-in-Chief William C. Banks for their efforts. I would like to take… Continue reading Will Soper Responds to Tyler Smotherman’s Review of “Greytown Is No More!”
A Bellicose Founding Charter: The US and Providing for the “Common Defence”
In this book review, the author analyzes Akhil Reed Amar’s The Words That Made Us: America’s Constitutional Conversation, 1760-1840. Specifically, the author focuses on Amar’s central thesis—that the fundamental reason behind the US Constitution was national security—and how that should affect our reading of the Constitution today. The author concludes that Amar’s book is noteworthy… Continue reading A Bellicose Founding Charter: The US and Providing for the “Common Defence”